Asymmetric Encryption

Asymmetric encryption, or public-key encryption, is a type of cryptographic protocol that uses a public and private key to exchange encrypted data between two users or devices.
The development of asymmetric encryption in the 1970s was essential to encrypting communications over the internet and remains a popular method for securing data.
Unlike symmetric encryption, which uses the same key for encryption and decryption, public-key cryptography employs a private key only known to the intended recipient of an encrypted message. Though asymmetric encryption is slower than symmetric encryption, the additional complexity makes a threat actor’s job infinitely more difficult for hacking the protected data.
This article looks at asymmetric encryption, how it works, its features, examples, and the history of public-key cryptography.
In this definition...
What is Asymmetric Encryption?
Asymmetric encryption is when two users exchange a mix of public and private variables over a network to produce a secure, trusted communication protocol for sharing data. This initial exchange, also known as a handshake, establishes a shared key for further communication.
Once connected, users send communications encrypted by the shared public key, which is only accessible to the unique recipient who holds the corresponding private key.
Asymmetric Encryption Features
- Two or more keys, one publicly accessible and one private to a user
- A handshake between two or more devices, which establishes communication
- Public and private user variables to create a shared key
- Extensive bit size and complex mathematical process to ensure security
- Paired with symmetric encryption for best of both worlds
Read more: Best Encryption Software & Tools | IT Business Edge
How Does Asymmetric Encryption Work?
The public-key handshake is a complex mathematical process to ensure access while denying prying eyes on public networks. The original Diffie-Hellman-Merkle method uses modular arithmetic as presented in the below infographic and in-depth explanation:
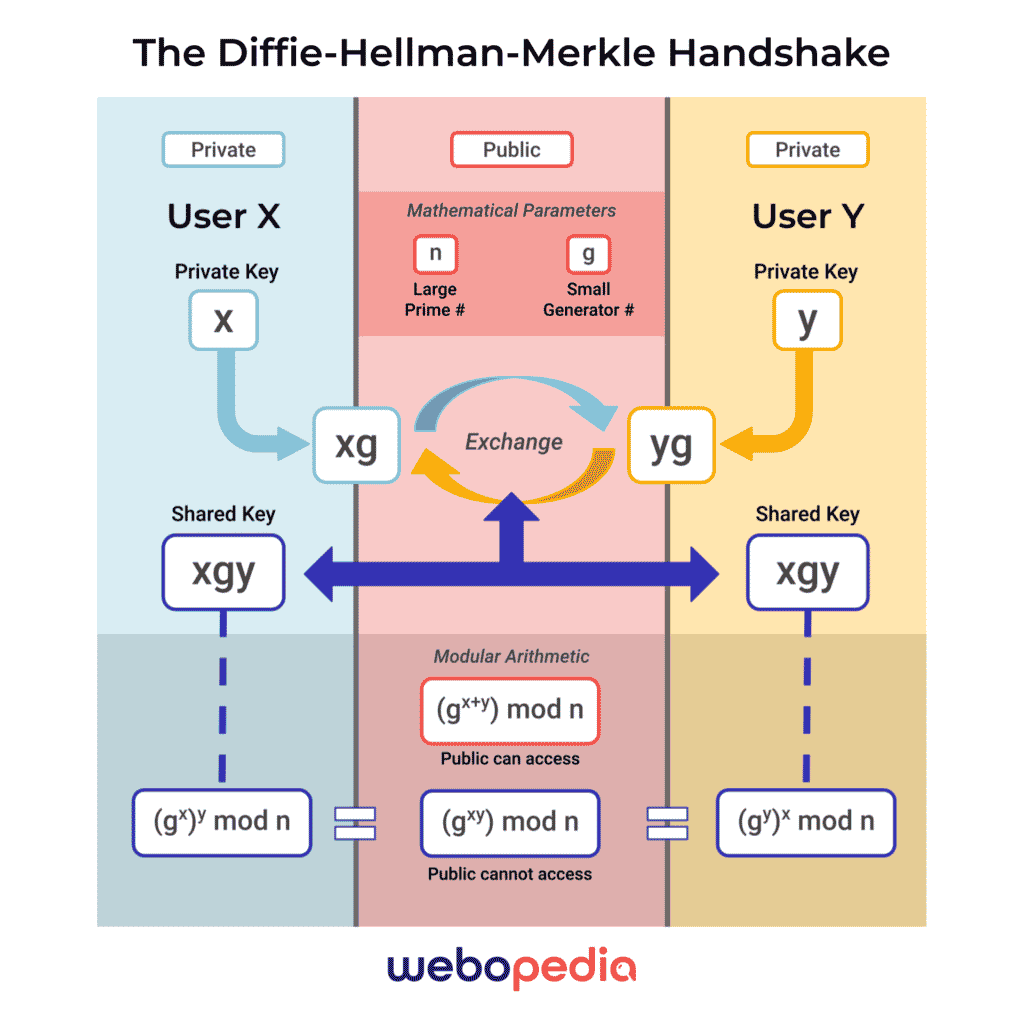
1. Agreement of Parameters
- Two users agree to public mathematical parameters designated by (n) and (g)
- (n) represents a large prime number that’s 2,000 to 4,000 bits long
- (g) represents a small number and serves as a generator
2. Private Key Infusion & Exchange
- Both users have private keys, never shared within public traffic, designated by (x) and (y)
- Combining the private key with the generator (g) creates public keys: (xg) and (yg)
- While visible to the public, it’s extremely difficult for threat actors to abstract the private keys – (x) and (y) – from the new publicly available keys, (xg) and (yg)
- Each user now has access to the other public-private key combination, which combines to form a symmetrical key (xgy)
3. Securing Communications from Outsiders
- Through (xgy) users can encrypt and decrypt messages using their private key
- With access to (xg) and (yg), threat actors can combine these numbers, but the result is (xggy), with the additional generator component mixed in
- Mathematically, actors can produce the formula for (xggy) as (gx+y) mod n; meanwhile, the legitimate key for (xgy) is (gxy) mod n
- Asymmetric encryption isn’t unbreakable but often requires brute force attempts
Also read: Top 10 Full Disk Encryption Software Products | eSecurity Planet
Asymmetric Encryption vs. Symmetric Encryption
Before asymmetric encryption was developed, symmetric encryption allowed for encrypted communication through a single shared key.
In symmetric encryption, users can grant access to encrypted messages by sharing a specific private key. This shared key method is faster, uses fewer bits, and requires less overhead, but it isn’t as effective in securing data for larger networks.
Asymmetric encryption provides more robust security for data at rest and in transit, but with more bits and a longer process, it isn’t as fast as symmetric encryption methods.
Asymmetric vs. Symmetric Encryption: Comparison Table
| Asymmetric Encryption | Symmetric Encryption | |
| Keys | 2 – Public and Private | 1 – Private |
| Bits | 2,048 to 4,096 | 128 to 256 |
| Speed | Slower | Faster |
| Overhead | More Complex, Expensive | Less Complex, Expensive |
| Security | Strong | Limited |
| Examples | Diffie-Hellman, RSA, ECC, DSA | AES, RC4, 3DES, QUAD |
Best of Both Worlds: Asymmetric and Symmetric Encryption
Web developers and cryptographers increasingly use both encryption methods, leveraging the speed provided by symmetric encryption and the security provided by asymmetric encryption.
Hybrid encryption systems often use asymmetric encryption to establish a trusted connection with another user, followed by symmetric encryption for subsequent communications. The Transport Layer Security (TLS) protocol is one of the most visible examples of hybrid encryption, with its extensive implementation for instant messaging, VoIP, email, and other web services.
Read more: End-to-End Encryption: Important Pros and Cons | CIO Insight

History of Asymmetric Encryption
Before the internet boom, encryption for distributed networks hit a tipping point with the development of public-key cryptography in the 1970s. In 1976, three computer scientists at Stanford—Whitfield Diffie, Martin Hellman, and Ralph Merkle—published their research and dubbed it the Diffie-Hellman-Merkle (DHM) key exchange.
Shortly after, three computer scientists at MIT—Ron Rivest, Adi Shamir, and Leonard Adelman—formulated a system for public-key cryptography, named the RSA algorithm. Both methods remain two of the most popular for asymmetric cryptography; however, RSA includes a digital signature component for authenticating users.
Examples of Asymmetric Encryption
Asymmetric encryption algorithms are essential to establishing the communication protocol between two parties and generating public and private keys. Here are some of the most common examples:
Pretty Good Privacy (PGP)
In 1991, cryptographer Phil Zimmerman developed the hybrid encryption protocol, Pretty Good Privacy (PGP), known for its extensive use in securing email communications. Symantec acquired PGP Corporation in 2010, but an OpenPGP-based open source version, GNU Privacy Guard (GPG), is a popular and actively maintained Linux distro.
Transport Security Layer (TLS)
The successor to the Secure Sockets Layer (SSL), TLS often incorporates a public-key infrastructure (PKI) and digital certificates to secure web browser communications.
Also read: 5 tools to make encryption key management easier | TechRepublic
Secure Shell Protocol (SSH)
Developed in the mid-1990s to replace Telnet and Unix shell protocols, the Secure Shell Protocol (SSH) allows network and server administrators to create a secure tunnel for managing remote devices.
Cryptocurrency
Part of cryptocurrency’s appeal is the security ensured by cryptographic algorithms and hashes. Popular coins like Bitcoin employ public-key encryption to enable the secure sending and receiving of funds from different user addresses.
This article is an update originally written and published by Vangie Beal on October 17, 1996.
Recent Coverage
- How Ransomware Uses Encryption – And Evolves | eSecurity Planet
- Data Security: Tokenization vs. Encryption | IT Business Edge
- How to Prevent Ransomware Attacks: 20 Best Practices | eSecurity Planet
- Enterprise End-to-End Encryption is on the Rise | IT Business Edge
- NordLocker vs VeraCrypt | Encryption Software Comparison | TechRepublic
- 83% of Companies Don’t Encrypt All Sensitive Data in Cloud | Datamation
- The Case for Decryption in Cybersecurity | eSecurity Planet
- Check Point vs Trend Micro | Encryption Software Comparison | TechRepublic
- The State of Blockchain Applications in Cybersecurity | eSecurity Planet
- What is Full Homomorphic Encryption (FHE) | CIO Insight

