Mobile Information Management (MIM) refers to software and services used to secure and manage the sensitive, often business-critical data used in the enterprise on mobile devices like smartphones and tablet computers.
Also referred to as Mobile Content Management (MCM), Mobile Information Management falls under the umbrella of Enterprise Mobility Management along with other mobile security initiatives like mobile device management (MDM) mobile application management (MAM) and mobile security management (MSM).
How Mobile Information Management Works
MIM is distinguished from other mobile security initiatives in that it focuses specifically on data rather than on the devices or applications that utilize the data. Mobile Information Management involves the encryption of sensitive data and ensuring that only authorized applications can access, transmit or store this data using strong password protection.
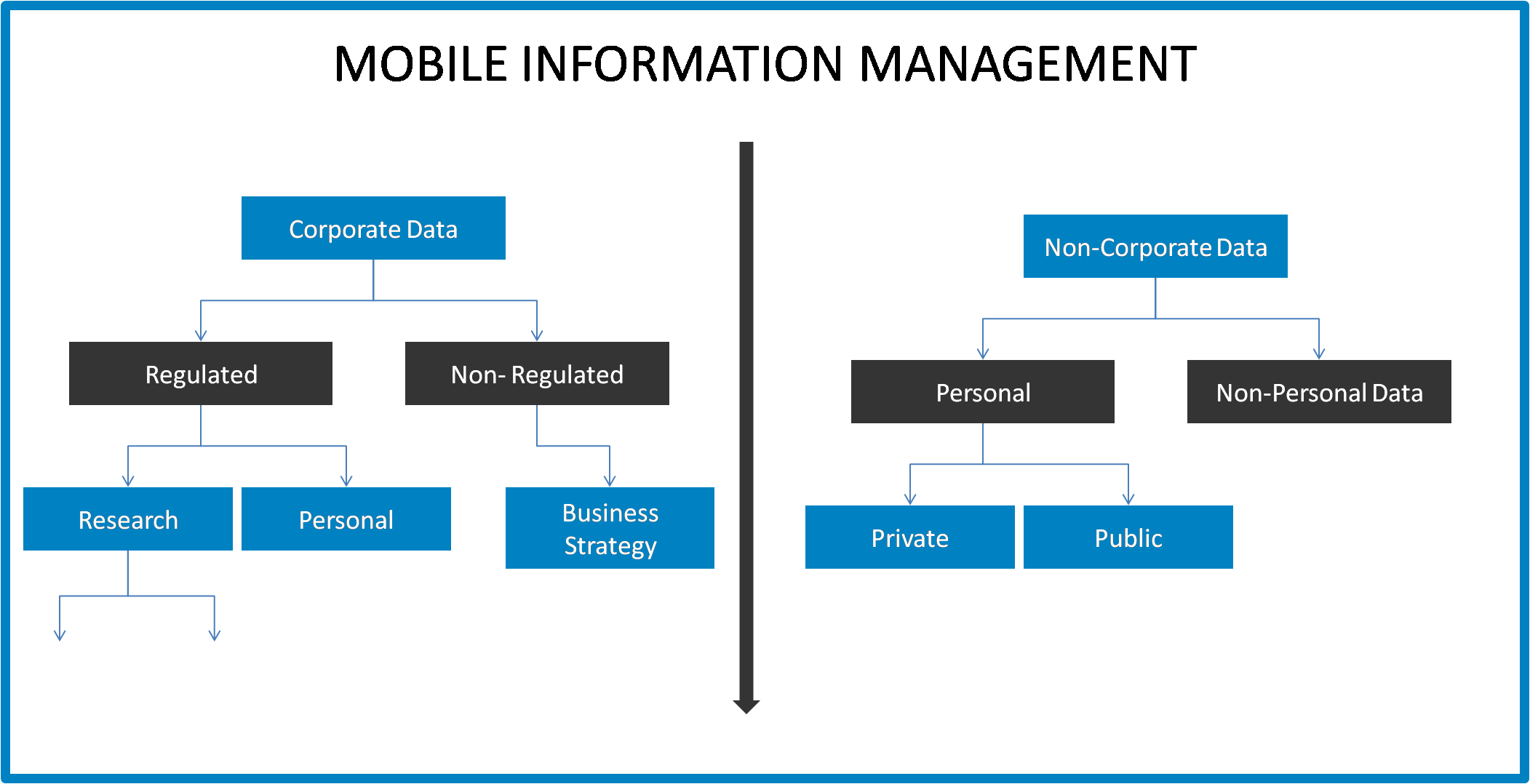
Source: Nestweaver
Well-rounded mobile information management strategies and solutions also include clear communication and enforcement of the MIM policies for protecting and securely using data on mobile devices in the enterprise.
On-premises mobile information management vendors and solutions available today include Nomadesk, RES HyperDrive and Citrix ShareFile, and public cloud services like Dropbox, Box, Microsoft SkyDrive and Google Drive can also be brought into an enterprise s MIM and overarching EMM strategies.
Mobile Information Management vs. MAM and MDM
Mobile Information Management shares some characteristics with both Mobile Application Management and Mobile Device Management, and MIM is frequently combined with MAM and/or MDM solutions as part of a holistic Enterprise Mobility Management strategy.
MDM primarily involves protecting and securing mobile device use within an enterprise as well as the use of applications on these devices whereas Mobile Application Management s specific focus is on securing sensitive enterprise apps and, when combined with MIM, the data utilized, stored and transmitted by these apps.

