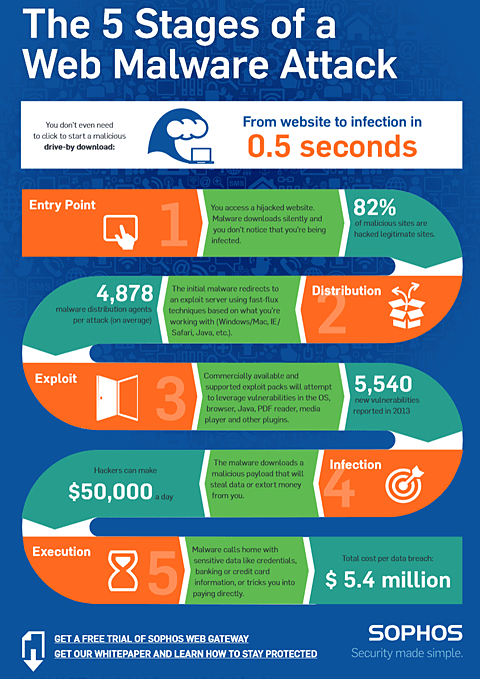
A drive-by download refers to potentially harmful software code that is installed on a person’s computer without the user needing to first accept or even be made aware of the software installation.
Drive-by downloads are a form of malware typically found on compromised web pages. By simply “driving by,” or visiting the web page, the drive-by download begins to download and is then installed in the background on the computer or mobile device without alerting the user.
How Drive-By Downloads Do Their Damage
Drive-by download hackers get users to visit their compromised web pages through web links on other web pages that appear to be normal and authentic. They also hide links to their drive-by download web pages in seemingly normal e-mails, text messages, and social media posts designed to attract users to drive-by download-infected web page content that looks authentic and uncompromised.
Drive-by downloads generally take advantage of security flaw exploits on browsers, apps, or operating systems that are out of date and haven’t been patched for the security flaws. As a result, keeping your operating system and its apps up to date helps minimize the risk of a drive-by download attack.
Additional Tips for Avoiding Drive-By Download Attacks
Security experts also recommend installing a high-quality internet security tool to help identify and prevent drive-by download attacks on your computer. Another recommendation is to avoid dubious links and offers that appear to be too good to be true, particularly when it comes to getting free content that you would normally have to pay for (pirated software or music, for example).